Authenticating Windows Active Directory users through LDAP to Jitsi Meet
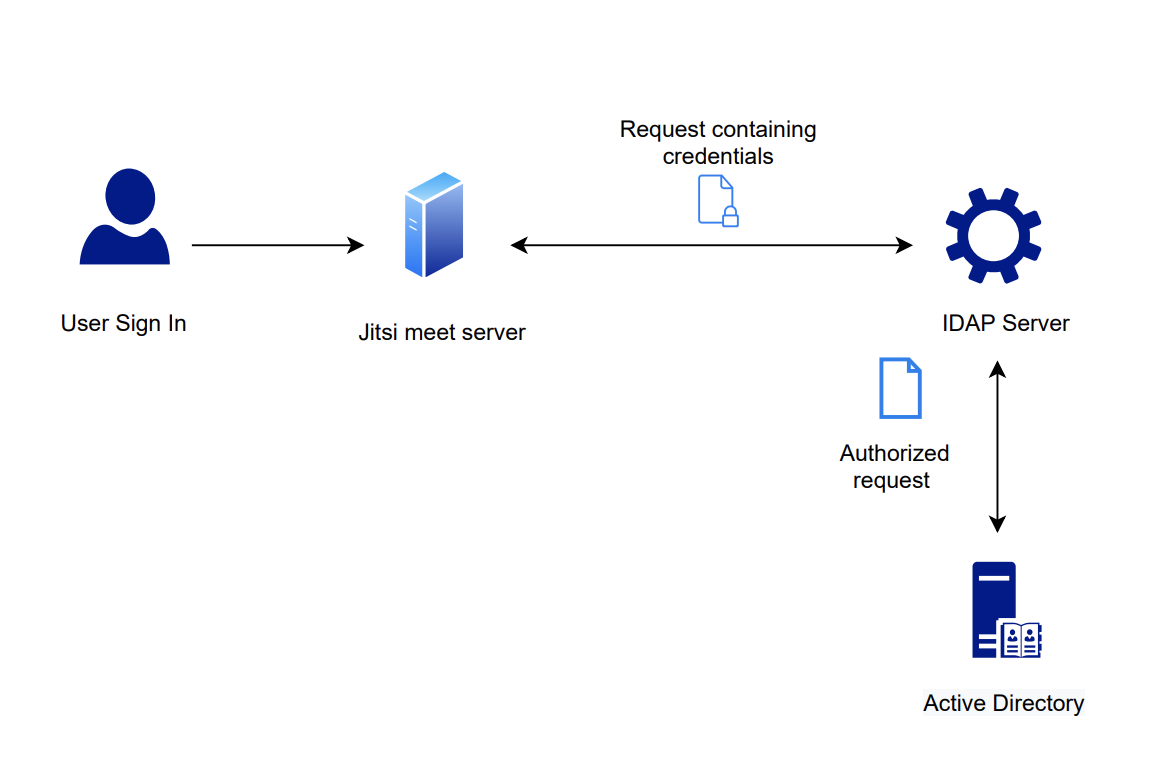
Active directory is Microsoft directory service which runs on Windows servers to enforce security standards across Windows operating systems by providing authorisation and authentication for computers, users, and groups.
The Lightweight Directory Access Protocol (LDAP) is a key element of Active Directory’s operation which is used to transfer information with other servers while providing directory services. It’s the mechanism to communicate with Active Directory and send messages between AD and other components of your IT infrastructure. It achieves this goal by storing data in the LDAP directory and authenticating the users before accessing the directory. Below diagram shows you how the authentication procedure flows among the user, servers and the active directory.
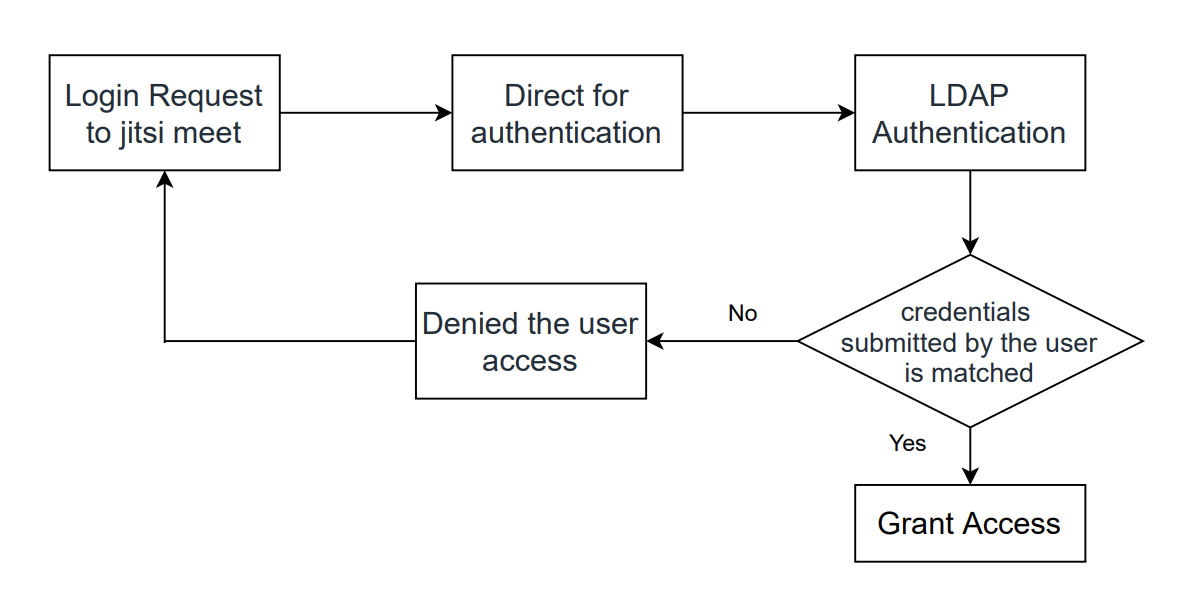
- Login Request to jitsi meet - client sends a request for information along with the user’s credentials
- Direct for authentication - Jisi meet server directs user credentials to LDAP server for authentication process
- LDAP Authentication - Authenticates the credentials submitted by the user against their core user identity (Active directory)
- Grant access to the user - If the credentials submitted by the user match, then grant access for user
- Denied the user access - If the credentials submitted by the user is not matched, then client is denied access
LDAP authentication setting configuration on jitsi meet
- Install the necessary
prosody-modulesand its recommendedlua-ldappackage
sudo apt-get install prosody-modules lua-ldap - manually install luarocks 5.2
-
install the SSL 1.0 headers
apt-get install libssl1.0-dev, followed byluarocks-5.2 install lualdap && luarocks-5.2 install luacrypto && luarocks-5.2 install jwt-jitsi - Configure the LDAP module in
/etc/prosody/conf.avail/ldap.cfg.lua -
Link the configuration into the config directory
ln -sf /etc/prosody/conf.avail/ldap.cfg.lua /etc/prosody/conf.d/ -
Add the following line to
/etc/prosody/prosody.cfg.luain order to allow BOSH connections when requiring encryption, even if unencrypted
consider_bosh_secure = true -
Enable LDAP authentication
edit/etc/prosody/conf.avail/jitsi.example.com.cfg.luaand change the
authentication to ldap2:
authentication = "ldap2" - Finally restart the modified service
sudo service prosody restart

Leave a Comment