Authentik - Developer Guide
Learn how to install and configure Authentik on AWS with our in-depth developer guide. This resource covers everything from initial deployment to advanced configuration options, ensuring a robust authentication solution for your applications

Welcome to the Meetrix Authentik Developer Guide! Authentik is an open-source Identity Provider designed for flexibility and versatility, making it an excellent choice for implementing sign-up, recovery, and other authentication features in your application. In this guide, we'll walk you through the step-by-step process of setting up Authentik from the AWS Marketplace. Let's dive in!
Video
Blog

Prerequisites
Before you get started with the Authentik AMI, ensure you have the following prerequisites:
- Basic knowledge of AWS services, including EC2 instances and CloudFormation.
- An active AWS account with appropriate permissions.
- Enough vCPU limit to create instance
(Follow https://meetrix.io/articles/how-to-increase-aws-quota/ blog to ensure this)
Launching the AMI
Step 1: Find and Select 'Authentik' AMI
- Log in to your AWS Management Console.
- Navigate to the 'Authentik' in AWS Marketplace.
Step 2: Initial Setup & Configuration
- Click the "Continue to Subscribe" button.
- After subscribing, you will need to accept the terms and conditions. Click on "Accept Terms" to proceed.
- Please wait for a few minutes while the processing takes place. Once it's completed, click on "Continue to Configuration".
- Select the "CloudFormation script to deploy Authentik" as the fulfilment option and choose your preferred region on the "Configure this software" page. Afterward, click the "Continue to Launch" button.
- From the "Choose Action" dropdown menu in "Launch this software" page, select "Launch CloudFormation" and click "Launch" button.
Create CloudFormation Stack
Step1: Create stack
- Ensure the "Template is ready" radio button is selected under "Prepare template".
2. Click "Next".
Step2: Specify stack options
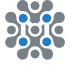
- Provide a unique "Stack name".
- Provide the "Admin Email" for SSL generation.
- For "DeploymentName", enter a name of your choice.
- Provide a public domain name for "DomainName" (Authentik will automatically try to setup SSL based on provided domain name, if that domain hosted on Route53. Please make sure your domain name hosted on route53. If its unsuccessful then you have to setup SSL manually).
- Choose an instance type, "InstanceType" (Recommended: t3.small).
- Select your preferred "keyName".
- Provide a S3 bucket name to "S3Bucket" for storing Database Backups.
- Set "SSHLocation" as "0.0.0.0/0".
- Keep "SubnetCidrBlock" as "10.0.0.0/24".
- Keep "VpcCidrBlock" as "10.0.0.0/16".
- Click "Next".
Step3: Configure stack options
- Choose "Roll back all stack resources" and "Delete all newly created resources" under the "Stack failure options" section.
- Click "Next".
Step4: Review
- Review and verify the details you've entered.
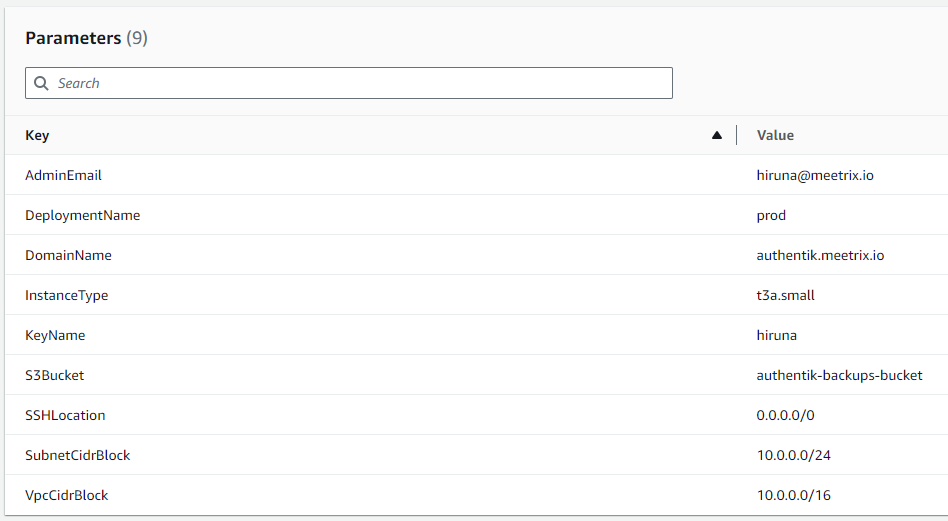
2. Tick the box that says, "I acknowledge that AWS CloudFormation might create IAM resources with custom names".
3. Click "Submit".
Afterward, you'll be directed to the CloudFormation stacks page.
Please wait for 5-10 minutes until the stack has been successfully created.
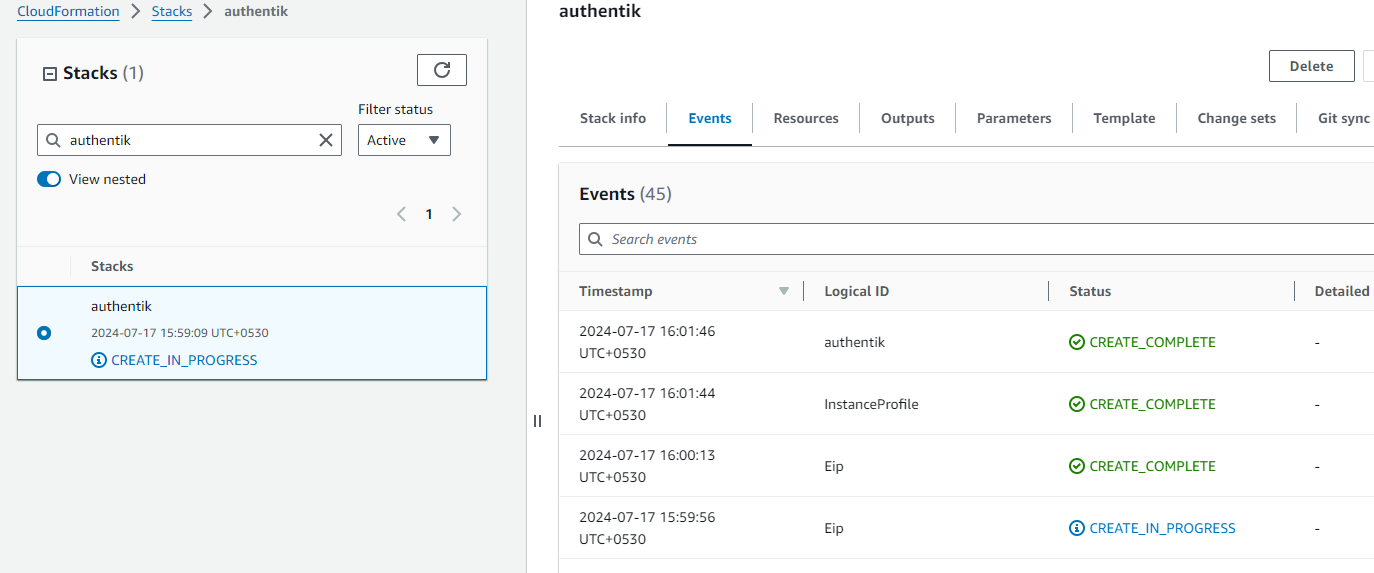
Update DNS
Step1: Copy IP Address
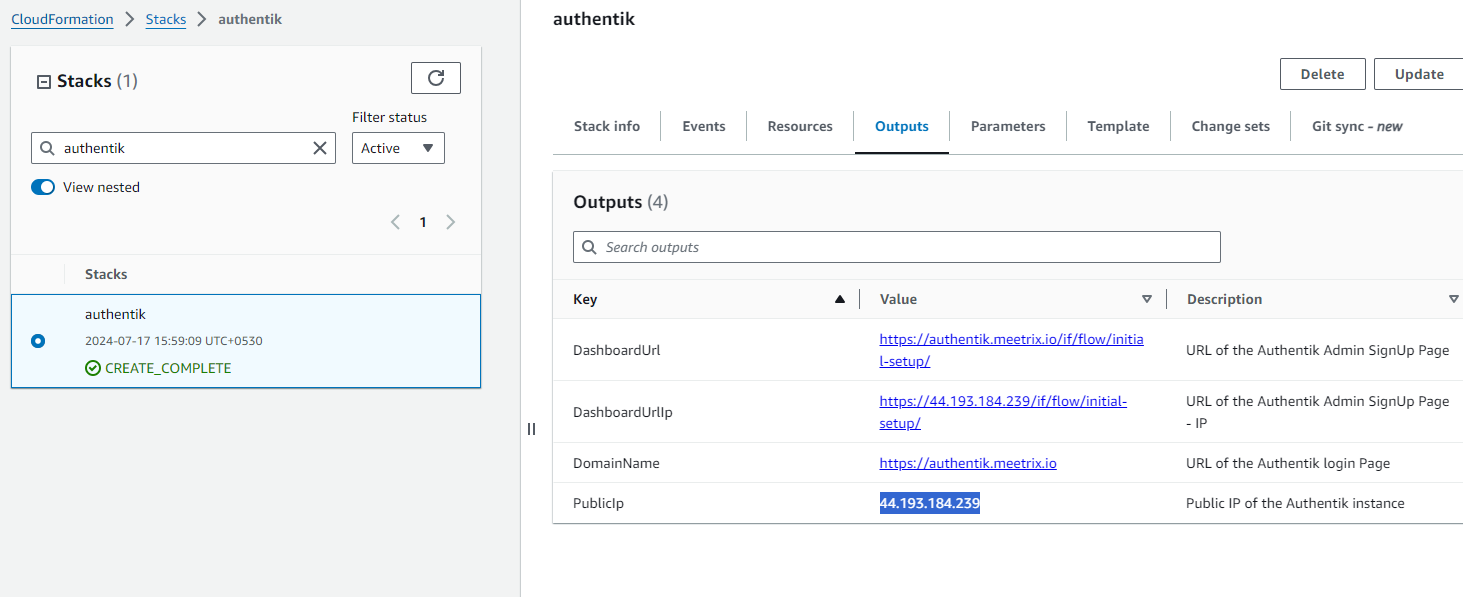
Copy the public Ip labeled "PublicIp" in the "Outputs" tab.
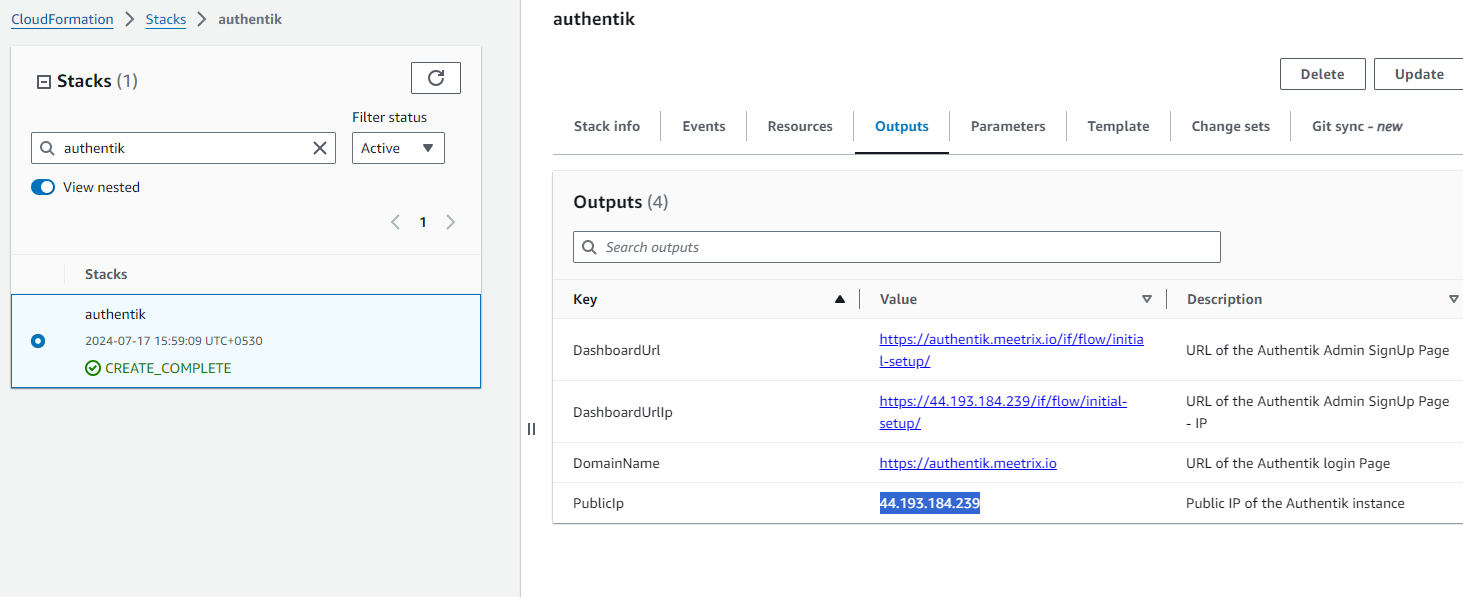
Step2: Update DNS
- Go to AWS Route 53 and navigate to "Hosted Zones".
- From there, select the relevant Hosted Zone for your provided "DomainName".
- Click on Create record.
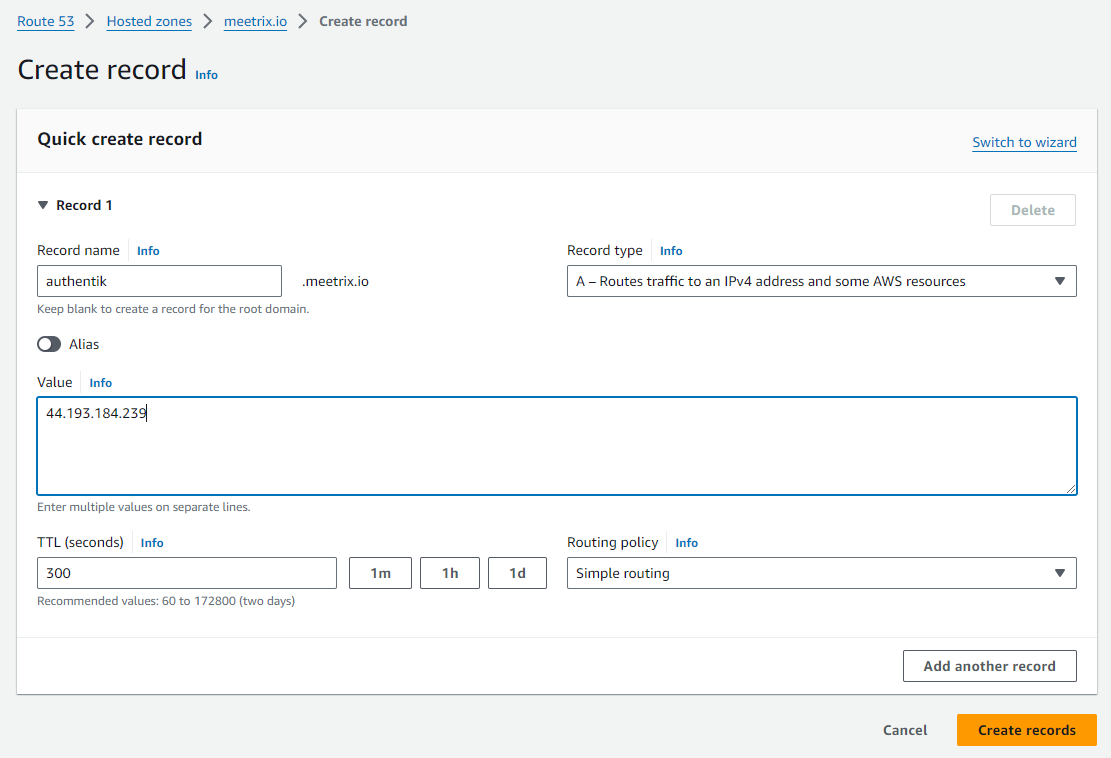
3. Add record name and then paste the copied "PublicIp" into the "value" textbox.
4. Click "Save".
Access Authentik
You can setup the Authentik application through the "DashboardUrl" or "DashboardUrlIp" provided in the "Outputs" tab. This will allow you to create an Admin account and all the future accounts will be created through the Admin panel.
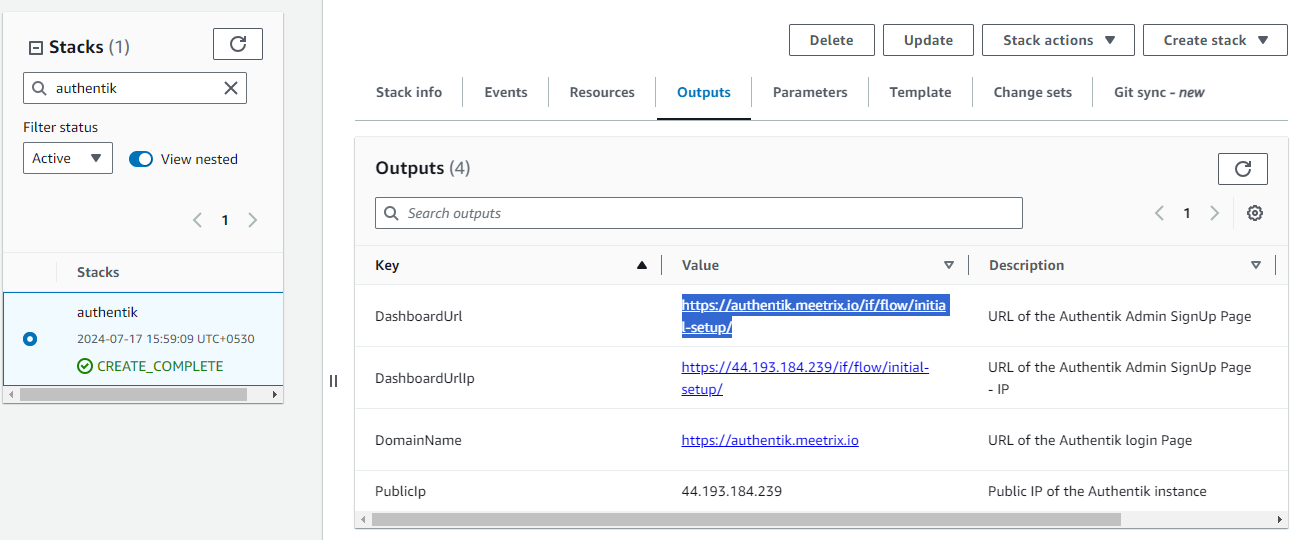
(If you encounter a "502 Bad Gateway error", please wait for about 5 minutes before refreshing the page)

Enter all the details and Click on Let's start button. Make sure to choose a strong password.
Once you have created admin login, use https://authentik.meetrix.io/ to log into the admin account.
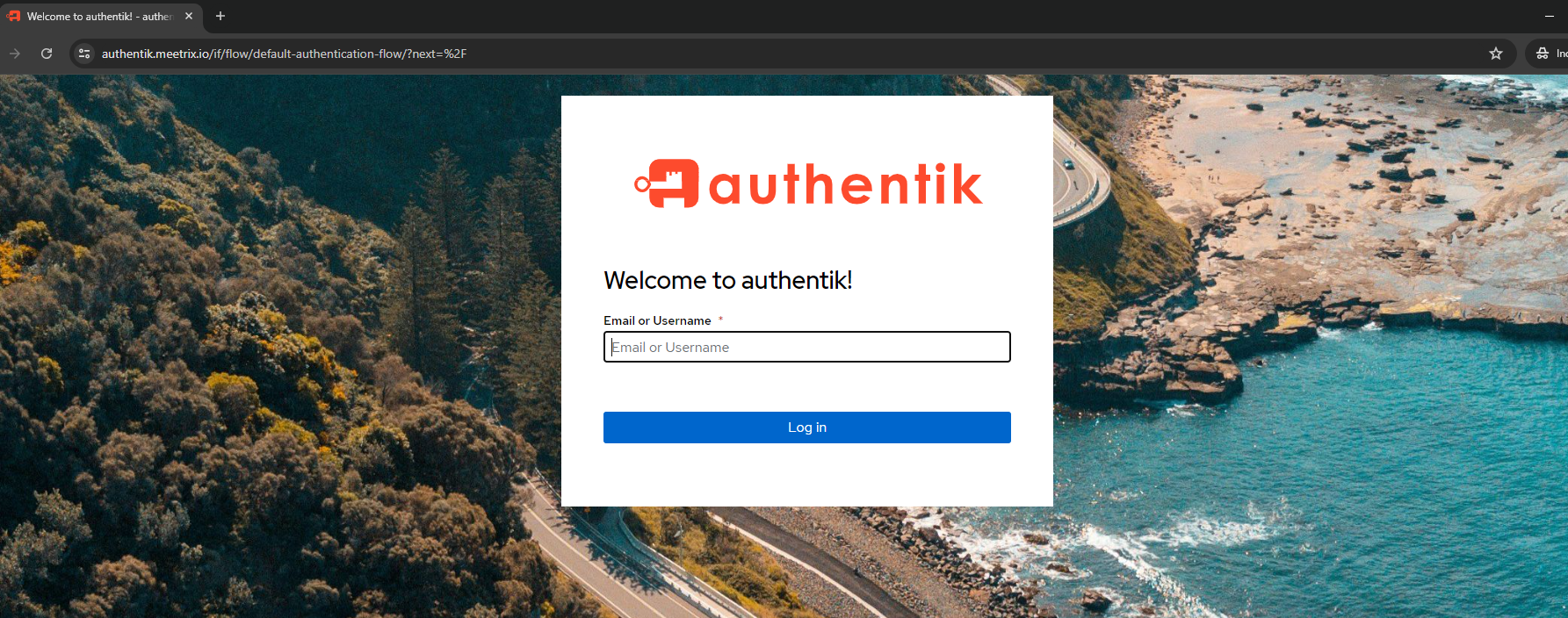
Generate SSL Manually
Authentik will automatically try to setup SSL based on provided domain name, if that domain hosted on Route53. If its unsuccessful then you have to setup SSL manually.
Step1: Copy IP Address
- Proceed with the instructions outlined in the above "Update DNS" section, if you have not already done so.
- Copy the Public IP address indicated as "PublicIp" in the "Outputs" tab.
Step2: Log in to the server
- Open the terminal and go to the directory where your private key is located.
- Paste the following command into your terminal and press Enter:
ssh -i <your key name> ubuntu@<Public IP address>.
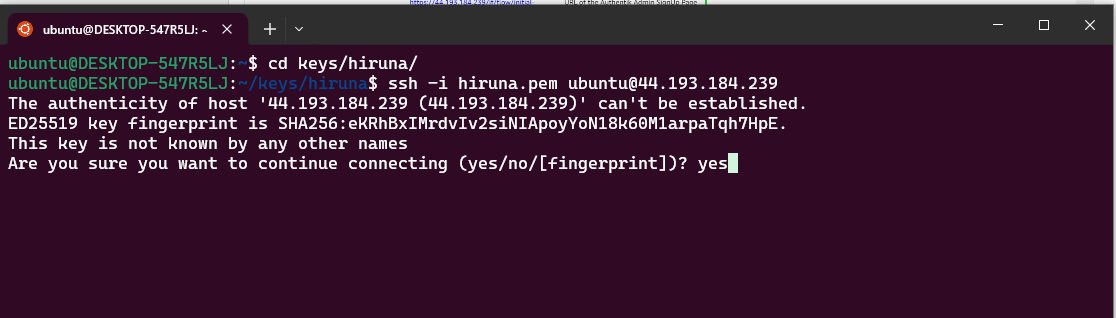
3. Type "yes" and press Enter. This will log you into the server.
Step3: Generate SSL
Paste the following command into your terminal and press Enter and follow the instructions:
sudo /root/certificate_generate_standalone.sh
Admin Email is acquiring for generate SSL certificates.
Shutting Down Authentik
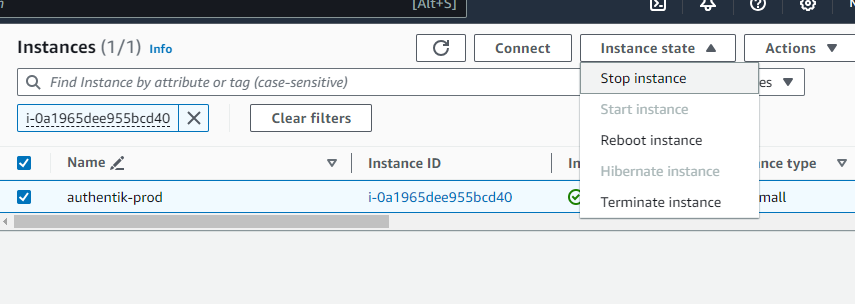
- Click the link labeled "Instance" in the "Resources" tab to access the EC2 instance, you will be directed to the Authentik instance in EC2.
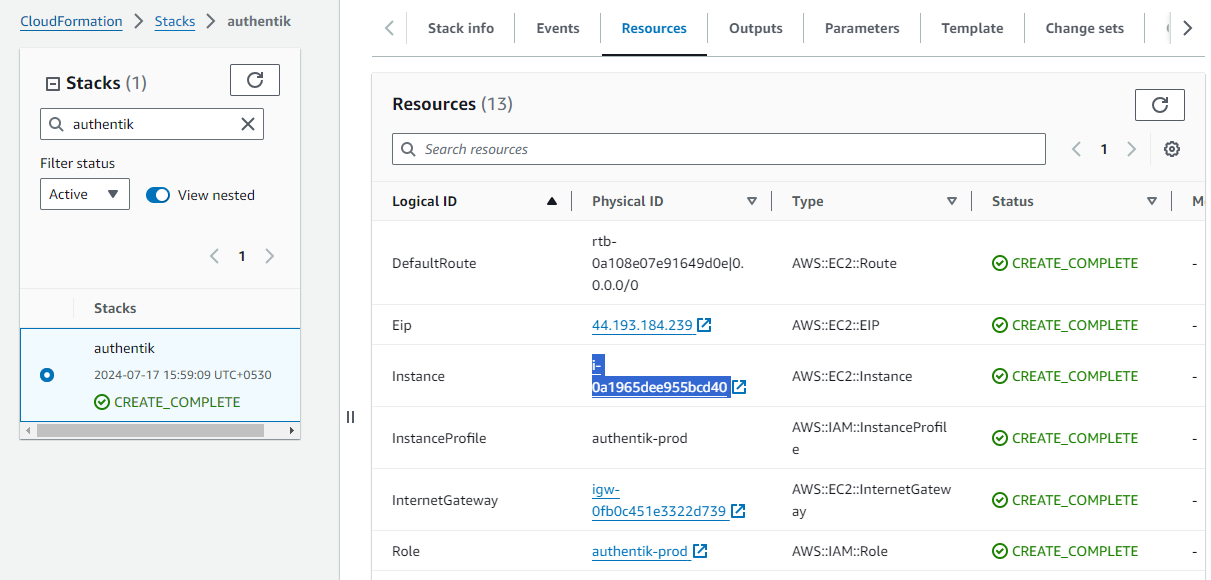
2. Select the Authentik instance by marking the checkbox and click "Stop instance" from the "Instance state" dropdown. You can restart the instance at your convenience by selecting "Start instance".
Remove Authentik
Delete the stack that has been created in the AWS Management Console under 'CloudFormation Stacks' by clicking the 'Delete' button.
Conclusion
The Meetrix Authentik Developer Guide is your essential resource for effortlessly integrating Authentik into your projects. Whether you're a seasoned developer or just beginning, our guide offers detailed, step-by-step instructions for setting up Authentik from the AWS Marketplace. Authentik stands out with its flexibility and versatility, seamlessly integrating into existing environments and supporting new protocols. It's an excellent solution for handling sign-up, recovery, and other authentication features, saving you the trouble of managing them yourself. With the Meetrix Authentik Developer Guide, you'll efficiently utilize Authentik's capabilities to create secure and robust authentication systems for your applications.
Technical Support
Reach out to Meetrix Support (aws@meetrix.io) for assistance with Authentik issues.